Make Data Theft Irrelevant. Anchor It™
Anchor’s file security platform is built on zero trust principles to secure and control your sensitive files, but remain invisible to end users.

Anchor Named Gold Winner in Data Security Platform and Best Cybersecurity Startup
Companies that Anchored data












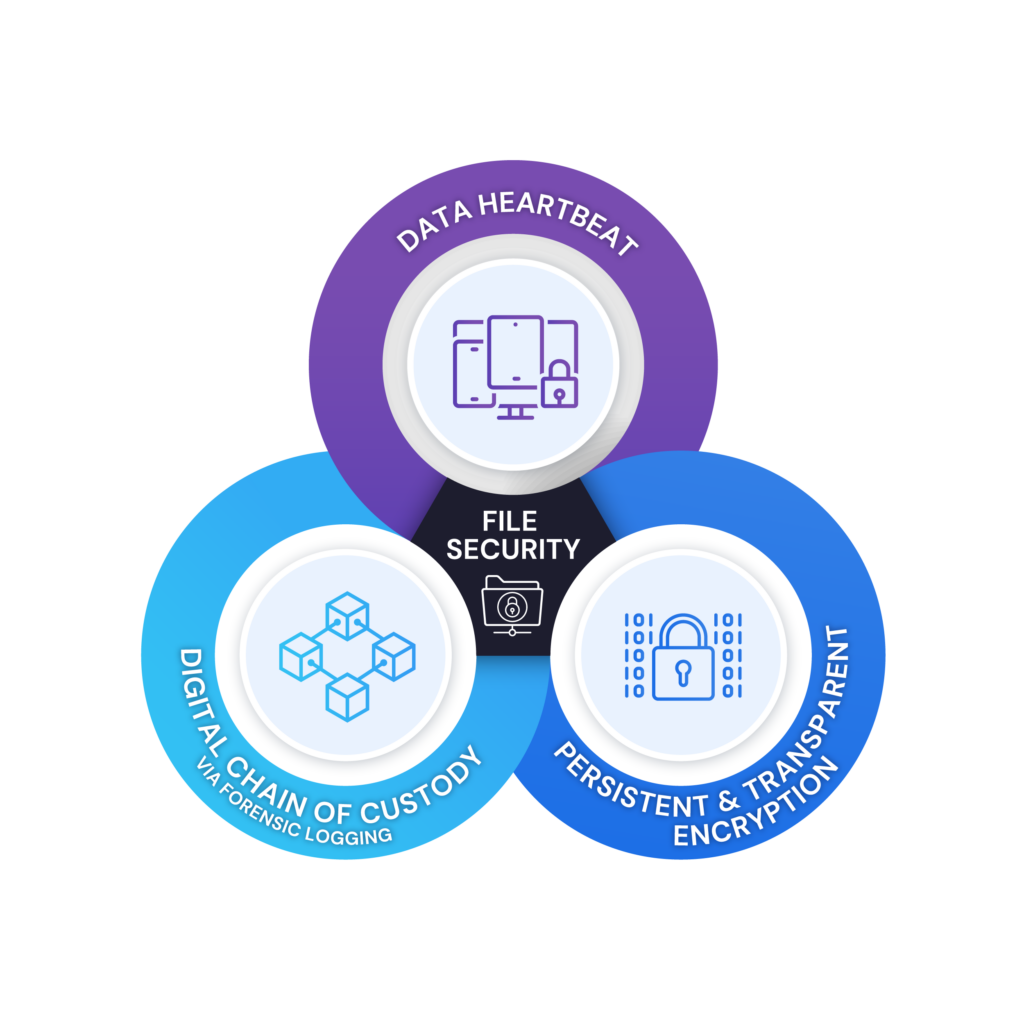
WHAT IS ANCHOR?
Patented combination of 3 powerful technologies
Anchored data is self–protecting. Each Anchored file is individually FIPS-validated encrypted at rest, in transit, and even while in use (saving does not generate plain text). Even if the files are stolen, they would never be more than cypher text due to our encryption process. Anchor uses Advanced Encryption Standard (AES) 256-bit military-grade encryption to provide a high level of encryption.
Patented heartbeat technology constantly verifies access rules in real-time based on a myriad of data sources such as Active Directory, geo-location, etc. When an access rule is broken, Anchor instantly revokes access. Even while the file is in use. Trust is never assumed, even after a file is open. Data protection at its best.
Real-time tracking of sensitive data. Audit trails of each request, including physical location. A true chain of custody for digital data.
Advanced Data Protection Platform
WHY ANCHOR?
More than just file encryption. More than just DLP.
Traditional cybersecurity focuses on locking down networks, devices, and people. All of this is done in the name of data security. But, once individual files are moved, shared, or stolen, the data is no longer protected. Even worse, these controls get in the way and frustrate business users to the point they intentionally work around them.
Anchor’s data protection platform inverts the equation by baking protection into the data, invisible to the business users (like antivirus), so that files are free to travel (even on mobile devices) and data security is out of the way.
85%
Employees admitted taking company documents
78%
Internal data theft motivated by financial gain
80%
Ransomware attacks in 2021 involving exfiltration of data
HOW TO ANCHOR?
Protect your data in 3 simple steps
Anchor’s data protection makes security easy and collaboration safe.
Choose what you want to protect
Pick who gets access
Select how it can be accessed
WHAT WE DO?
Anchor brings world-class data security to everyday users.
Anchor is a simple, turnkey, low-cost way for organizations to achieve state-of-the-art data security without getting in the way
Thwart Cyber Crime
Ransomware attacks come on multiple fronts. You defend against two threats today: data lockout and denial of service. Prevent the criminals from stealing your files and selling it back to you or your competitors.
Protect the People
DLP solutions don’t work. Prevent well-intentioned employees from doing things like sending sensitive documents to their personal email accounts without interfering with appropriate business collaboration.
Employees Exit, Data Stays
Prevent exiting employees from walking into their new job with your documents, designs, customer lists, etc.
Add a Critical New Layer to Security
Firewalls, NTFS Permissions, and MDM are not enough. Bake Zero Trust principles like MFA directly into your files to protect your sensitive financials, PHI, PII, trade secrets, and other intellectual property.
Reduce Cyber Liability
Cyber Insurance premiums are rising, as well as the requirements for obtaining coverage. At the same time, coverage is reducing. Most insurance companies require MFA to get coverage and exclude paying ransoms for data that is stolen. Satisfy MFA while also eliminating the ability for your data to be stolen and used against you.
INDUSTRIES WE SERVE
Proudly Protecting Information-Critical Industries
We help protect and control sensitive data for the world’s most information-critical industries such as…
- Defense Industrial Base
- Manufacturing
- Healthcare
- Financial Services
- Legal Services
- Consulting Services
The Department of Defense now requires Cybersecurity Maturity Model Certification (CMMC) for private contractors, including subcontractors. This means get your cybersecurity in order or you can no longer bid on defense contracts. Anchor helps achieve CMMC compliance without changing the way you operate or disrupting your business.
Anchor Controlled Unclassified Information (CUI)
- Checks many CMMC boxes
- Minimal impact on the user
- Works with what you have
- File-level granularity
- CUI always encrypted
- Automatic instant revocation
- Detailed access audit trail
- Easy secure file sharing
The companies who build the world we know and love have experienced rapid digital transformation and deal with increasingly complex supply chains. We protect the intellectual property they depend on from CAD, CAM, BIM, product, process, and more.
Simple, Employee-Friendly Data Security.
Anchor provides powerfully simple data security for CAD, engineering, 3D modeling, project management and a multitude of other software you depend on. Other security “solutions” force you into limited environments in the cloud just to keep your data safe, slowing down your team. Anchor bends over backward to work seamlessly in your environment without getting in your way.
Give patients the care they deserve. Let Anchor handle the rest.
We understand that patient care is the number one priority. That’s why Anchor makes it easy to share and protect PHI. Anchor lets you focus on doing what you do best, which is giving quality care. With Anchor, you won’t have to worry about sensitive data being stolen, because we encrypt the data itself. Only users who follow access rules are able to read the content of the data. Anchor works in the background, without changing how you work. Rest easy knowing that your data will be secured with one of the strongest forms of encryption, military-grade protection.
How Anchor Supports HIPAA
Anchor’s built in classification system and true data-centric security makes it easier than ever to manage and control PHI, even if it leaves your network. Sensitive data is identified and anchored. Only users who follow the access rules of the protected data are given access. If access rules are not met, the data remains encrypted with a military-grade cypher. Anchor works behind the scenes, remaining invisible to the user and not affecting the way they work. This means less effort at an affordable cost.
No Hassle With Anchor’s Password Free Protection.
Anchor offers strong, transparent data security that ensures your financial documents are protected from internal and external threats with military-grade encryption.
Keeping Financial Data Secure Has Never Been This Easy.
Financial departments deal with highly sensitive data, including credit card information, social security numbers, and bank details. It is important that appropriate security measures are taken in order to prevent the risk of a security breach. Anchor is the most cost-effective way to store financial data and doesn’t force you to dramatically change the way your department operates.
Attorney-Client Privilege
Every client file should be treated as confidential. That’s easy in the physical
world but how do you do it in digital world? An honest mistake can result in
serious problems for your firm.
It’s A Whole Firm Problem
Confidentiality isn’t just for attorneys. Anyone in the firm who has access to
client data can make a mistake. Your data control process must take the entire
firm into account in order to be effective.
Legal Reviews & Remote Work
As remote work has taken off and legal teams have become more distributed, we
need new tools and processes that can ensure the confidentiality of client
files, whether the work takes place at the office or in the living room.
Anchor Your Data
Anchor's strong encryption protects client file confidentiality from both outside attacks and bad
decisions made by insiders. It keeps files with confidential information encrypted and embeds powerfully simple rules to ensure they’re only opened as intended.
You can’t do business without collaborating on sensitive data. Anchor provides a secure collaboration for you, your clients, and your partners so each organization maintains absolute control over how, when, and under what circumstances their data is used.
How Anchor Supports Confidentiality
Anchor ensures that your clients’ confidential data and intellectual property are secure by allowing clients to anchor their data using complex algorithms. This means that only users who follow the access rules of the protected data are given access. If access rules are not met, the data remains encrypted with AES 256-bit encryption (military-grade cypher). We provide clients with a secure way to share their sensitive data when using consulting services. Anchor’s monitoring features let clients audit who is accessing their data and how. Anchor works behind the scenes, remaining invisible to the user and not affecting the way they work. This means less effort at an affordable cost.
FEATURE
Zero Trust Data Security
The world is connected and distributed. Data lives in the cloud and on IoT devices. Employees are working remotely and bringing their own devices. Bad actors are already inside the network. Networks and computers are no longer in the circle of trust. A zero-trust architecture (ZTA) is now the only way to be secure and have truly secure storage.
Anchor changes the game by shifting the paradigm from complex infrastructure security to simple individual file security. Our file encryption software actually eases the administrative burden while providing stronger protection for your sensitive data.
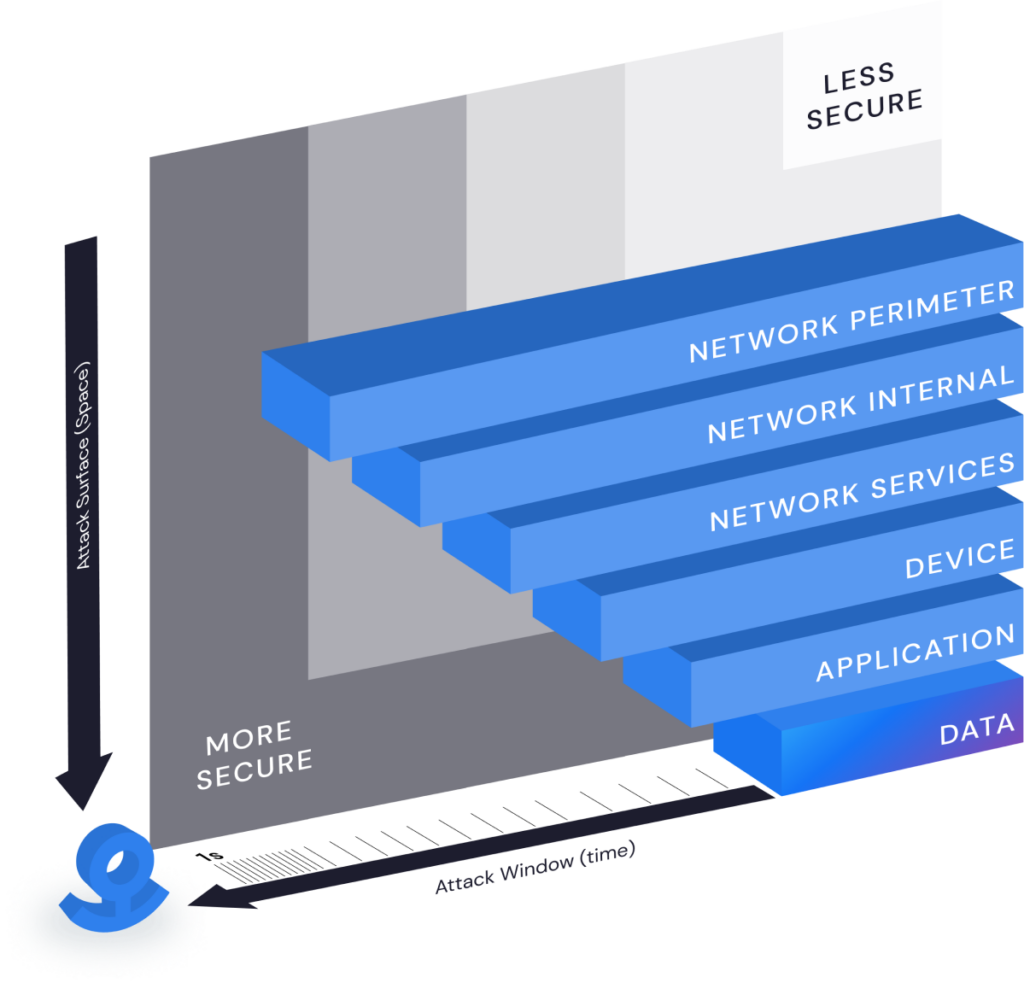
FEATURE
A Fortress for Every File
Zero trust architectures define micro-perimeters around protected resources in order to reduce the incentives and minimize the impact of a network breach. Anchor’s advanced encryption technology brings micro-perimeters to the file and removes the network from the equation entirely. With Anchor, every single file has its own independent security perimeter and every single request to use it is verified.
FEATURE
Continuous Authorization & Instant Revocation
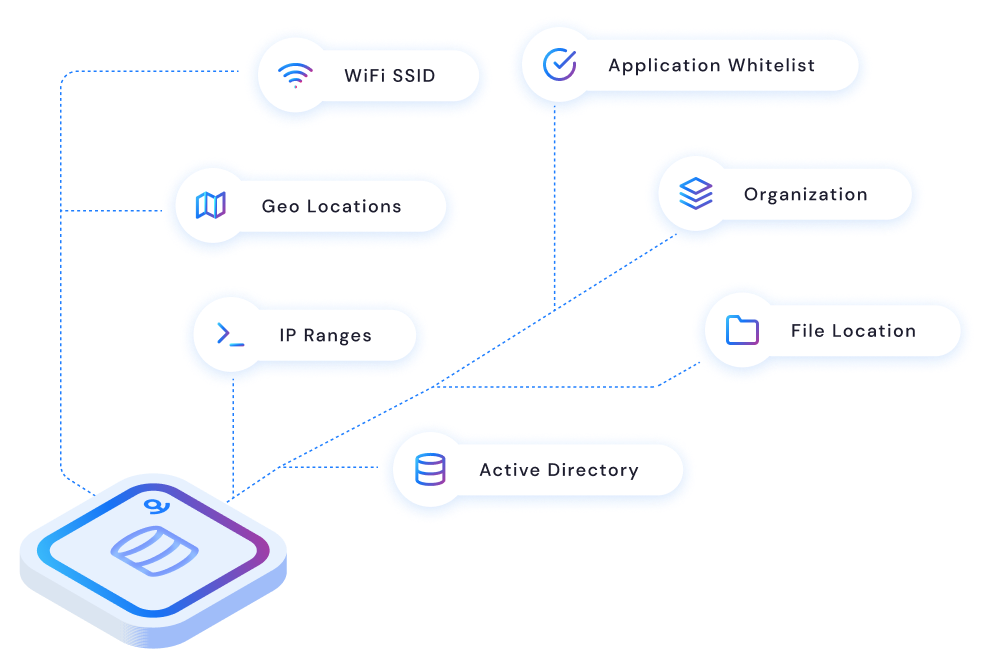
Zero trust principles dictate that policies should be dynamic, based on as many sources of data as possible. Anchor brings zero trust authorization to files. Patented heartbeat technology constantly verifies access rules in real-time based on a myriad of organizational and contextual data sources such Active Directory, Geo-IP, IP address, Wi-Fi network, and more. It’s multi-factor authorization for file access. When an access rule is broken on a file in use, Anchor instantly shuts it down. Trust is never assumed, even after a file is open. Encryption software at its best.
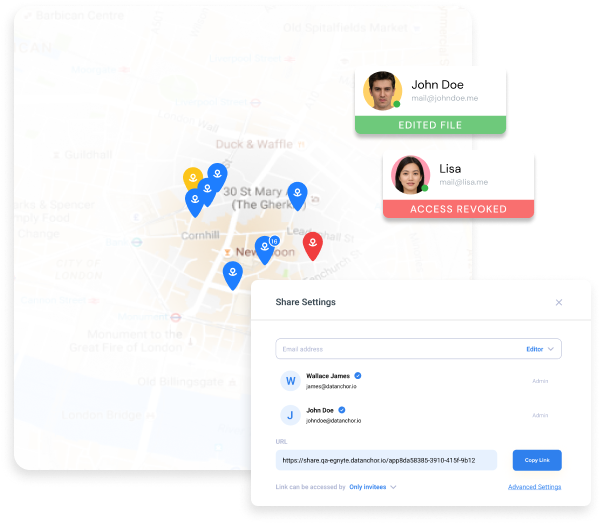
FEATURE
Share Access, Keep Control
Businesses share files to collaborate with others and create value. Too often, the recipients of that information misuse or abuse that data by leaving it unprotected, permanently retaining the information, or sharing it with unauthorized parties. Anchor is a lightweight solution that enforces zero trust security at the file level, based on the user, their role, and the context in which they’re trying to access data. It continues to protect and work with files outside an organization’s network just as well as it works inside, whether they have been shared or stolen. Anchor facilitates remote work and collaboration across the internet while maintaining strong protection against unauthorized data access. The perfect encryption software tool for today’s remote workforce.
FEATURE
Stop the Bad Guys, Not the Business
All over the world, businesses are increasingly under attack every day. In response to the ever-advancing threat organizations create more layers of security, via complex encryption programs, increasing the burden on the employees. This results in employees finding ways to circumvent those controls. Remember when password complexity requirements caused employees to write down their passwords and hide them under their keyboards?
Anchor protection is transparent to the end users and requires no workflow changes to how you use your applications today. The only time an end user is aware of the protection is when they use data in a way they are not allowed, like from a home computer.
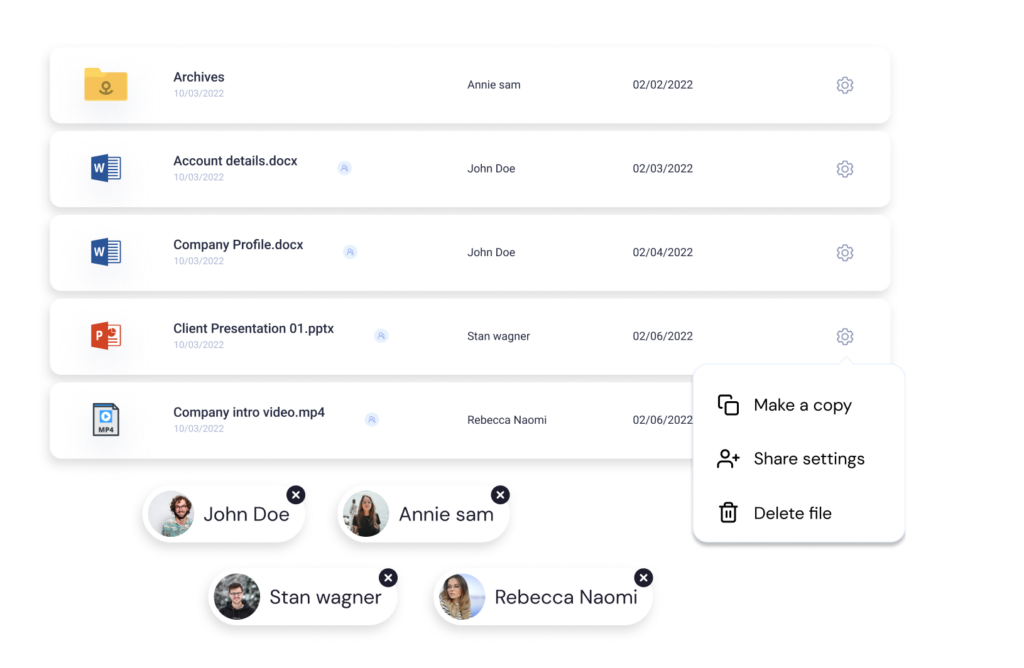
Control the data. Free the people.
Anchor is Simple, Transparent, and Affordable. Click “Get Started” below to see for yourself, in a matter of minutes. Or, if you prefer, click the link below to schedule a demo with our team.
LATEST NEWS
Latest news

Data Security Essentials: A Small Business Owner’s Guide to Protecting Sensitive Information

JOIN US THIS APRIL AT THE 16TH ANNUAL CENTRAL OHIO ISSA INFOSEC SUMMIT

Zero Trust Architecture: Building a Resilient Cybersecurity Framework for the Modern Enterprise
Anchor Wins Top Honor in Two Categories in the 2023 Cybersecurity Excellence Awards

Choosing the Right File Encryption Software: A Simple Guide
