Defense Contracting
Data security for defense contractors
When you have sensitive data, security must be built in
Data security ensures national security
Protecting CUI protects your business
As a defense contractor, your business has to address more than general cybersecurity concerns. Governmental standards and regulations such as DFARS, ITAR, and, more importantly, CMMC all mandate heightened data security
You have a significant burden that is under scrutiny. Your exchange of controlled unclassified information (CUI) with others in the defense supply chain exposes you to the threat of cyberattacks and intellectual property theft. This threat is a concern to not only national security but also your business.
The challenge of protecting CUI
DLP only adds complexity
Data loss prevention (DLP) may appear to be the obvious solution, but traditional complicated IT controls, like DLP, focus on locking down networks, devices, and people. They fail to protect data in three major ways: by only supporting some fle types, not all; not protecting data once files are moved, shared, or stolen; and getting in the way to the point that frustrated business users intentionally work around the controls or the business forces IT to dial back the protection.
The data security you need
Low cost, easy to implement, transparent experience
To achieve regulatory compliance, particularly CMMC, you need to continuously step up your data security game. You need a solution that is:
Simple
Quick to deploy and easy-to-use SaaS solution
Transparent Experience
Frictionless data security works in the background like antivirus
Bulletproof
Encrypted and 100% “self-protecting,” even if files are stolen.
Affordable
Impervious to attacks yet won’t force you to break the bank

Meet Cybersecurity Maturity Model Certification (CMMC) Compliance
Cybersecurity Maturity Model Certification (CMMC) is required of all defense contractors before they can bid on defense contracts. CMMC 2.0 defines 3 levels of cybersecurity maturity at which an organization can be certified. Defense contractors handling CUI must be CMMC level 2 certified. Contractors handling ITAR data must be CMMC level 3 certified.
CMMC data protection compliance made easy
Anchor protects the sensitive and confidential data you are entrusted with
- Helps attain CMMC compliance simply and affordably, AND without changing the way you operate or disrupting your business.
- Embeds protection into the data – Files can be moved because the data is self-protecting.
- Uses no controls that lock down networks, devices and people and frustrate business users.
- Brings affordable modern security to your existing infrastructure
- Simplifies your system architecture – Keep Controlled Unclassified Information (CUI) in Anchor-protected files instead of a complex system of networks and computers
- Shrinks the attack surface down to the CUI itself by protecting it directly with strong encryption and powerfully simple access control.
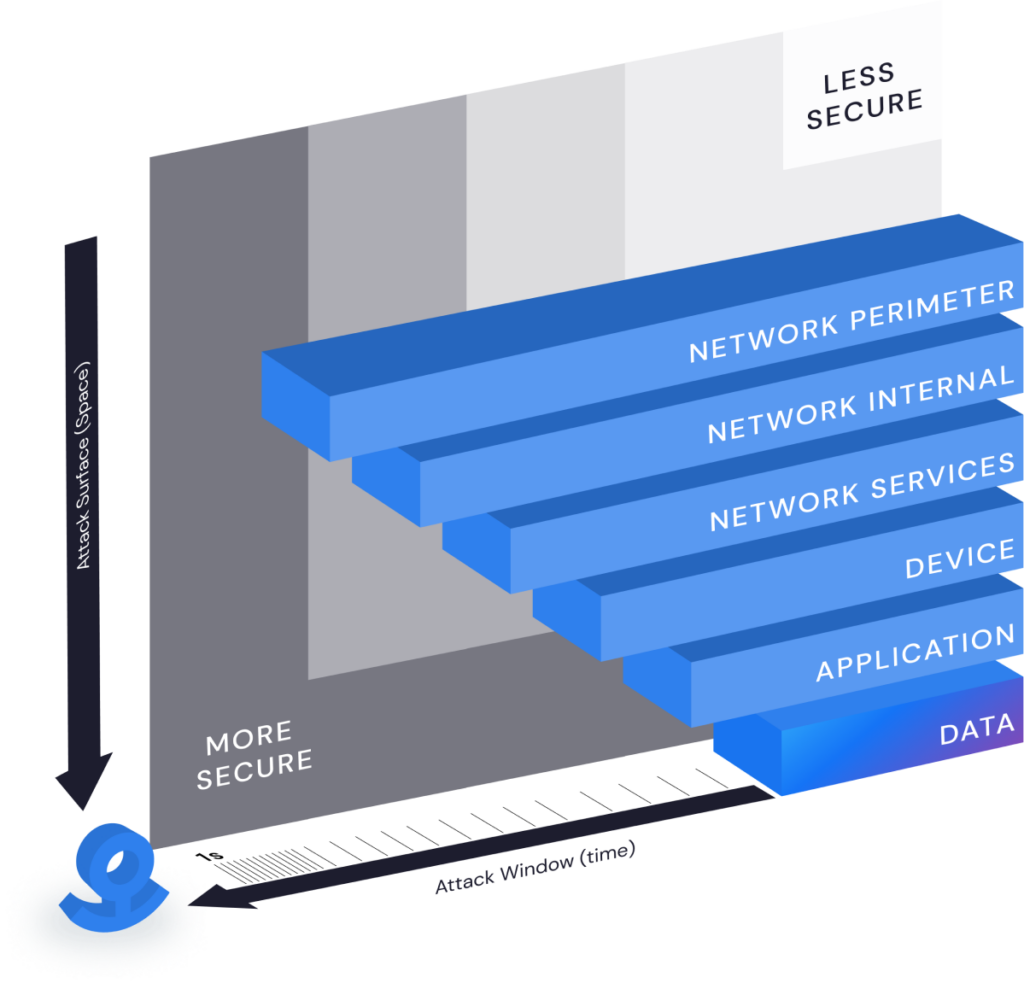

Learn about the Anchor Security Architecture for CMMC 2.0
This quick guide outlines CMMC requirements, provides examples of how Anchor works in various IT infrastructures and offers a detailed mapping exercise illustrating the domains and subdomains covered by the Anchor platform.
