
Data Can Protect Itself. Anchor It™
Anchor is a zero-trust platform that solves the weaknesses of traditional DLP.
- Deployable in minutes
- No changes to your workflow
- Encrypted in all states (in transit, in use, at rest)
- Invisible to end user
Anchor vs Traditional DLP
Download the Ebook
Protect your data in 3 simple steps
Choose what you want to protect
Pick who gets access
Select how it can be accessed
Stop the Bad Guys, Not the Business
All over the world, businesses are increasingly under attack every day. In response to the ever-advancing threat, organizations create more layers of security and increase the burden on the employees. This results in employees finding ways to circumvent those controls. Remember when password complexity requirements caused employees to write down their passwords and hide them under their keyboards?
Anchor protection is transparent to the end users and requires no workflow changes to how you use your applications today. The only time an end user is aware of the protection is when they use data in a way they are not allowed, like from a home computer.
Our Secret Sauce
Patented combination of 3 well-known technologies

Persistent and Transparent Encryption
Anchored data is self–protecting. Each Anchored file is individually FIPS-validated encrypted at rest, in transit, and even while in use (saving does not generate plain text). Even if the files are stolen, they would never be more than cypher text.

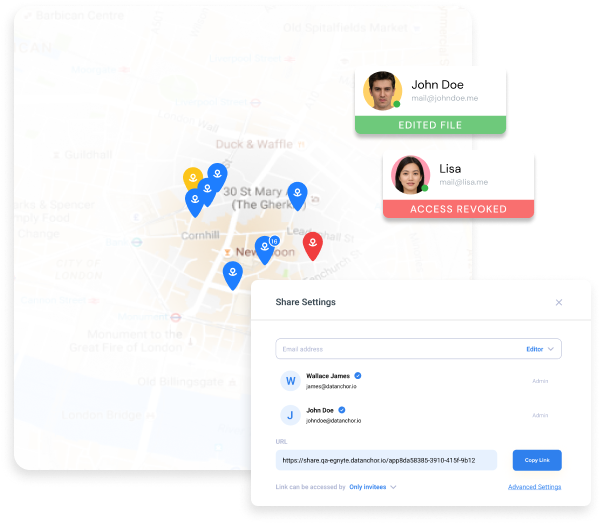
Multi-factor Access Controls
Patented heartbeat technology constantly verifies access rules in real-time based on a myriad of data sources such as Active Directory, geo-location, etc. When an access rule is broken, Anchor instantly revokes access. Even while the file is in use. Trust is never assumed, even after a file is open.

Digital Chain of Custody via Forensic Logging
Real-time tracking of sensitive data. Audit trails of each request, including physical location. A true chain of custody for digital data.