File Encryption Security, Simplified.
The Anchor file encryption solution:
 Encrypts Files
Encrypts Files
 Verifies Access
Verifies Access
 Logs an audit trail
Logs an audit trail
Serving businesses in:
- Defense Industrial Base
- Manufacturing
- Healthcare
- Financial Services
NO CHANGES TO YOUR
EXISTING WORKFLOW
How does data protect itself?
Stop the Bad Guys, Not the Business
Anchor is simple file encryption software that does not get in the way.
Simple file level encryption
Transparent data protection that doesn’t disrupt your business. Files encrypted at rest, in transit, and even in use.
Deployable in minutes
Security shouldn’t take months or years to implement. We secure your sensitive files in minutes. It’s really that simple!
DLP is great, but is there something better?
Data Loss Prevention (DLP) has been the industry standard for protecting data.
Sure a DLP policy protects files but at the expense of a business’s networks, devices, and people.
Because of that, more than 35% of large DLP implementations fail.

ENTER ANCHOR...
Anchor's solution to the problems with DLP is Self-Protecting Data.
Find our more with our free Anchor vs. DLP eBook below:
Why Anchor?
Advanced file encryption tool
Rapid
Implementation
deployable in minutes

User Transparency
security measures are baked-in and run silently in the background
Cost Effective
with minimal implementation or maintenance resources required

Data Protection In All States

Strong encryption software that protects at rest, in transit, and even while in use
Trusted by






File Security in 3 Steps
Choose what you want to protect

Pick who you want to access it

Select how you want them to access it

Powered by 3 Prominent Technologies
Persistent and Transparent Encryption
Anchored data is self–protecting. Each Anchored file is individually FIPS-validate encrypted at rest, in transit, and even in use (saving does not generate plain text). In the worst case, if files are stolen, they would never display more than cypher text.
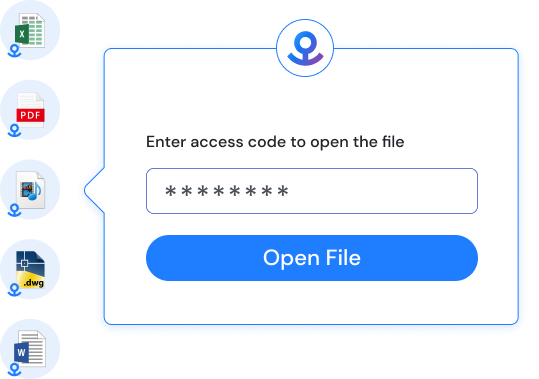
Multi-Factor Access Controls
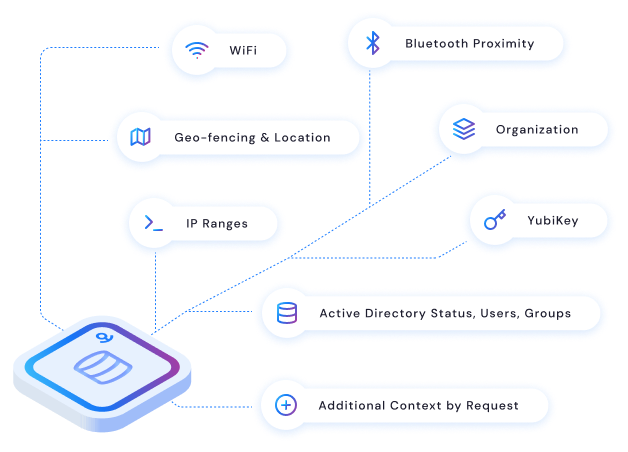
Our patented HEARTBEAT TECHNOLOGY® constantly verifies access rules in real-time, based on a myriad of data sources such as Active Directory, geo-location, and more. When an access rule is broken, Anchor instantly revokes access. Even while the file is in use. Trust is never assumed, even after a file is open.
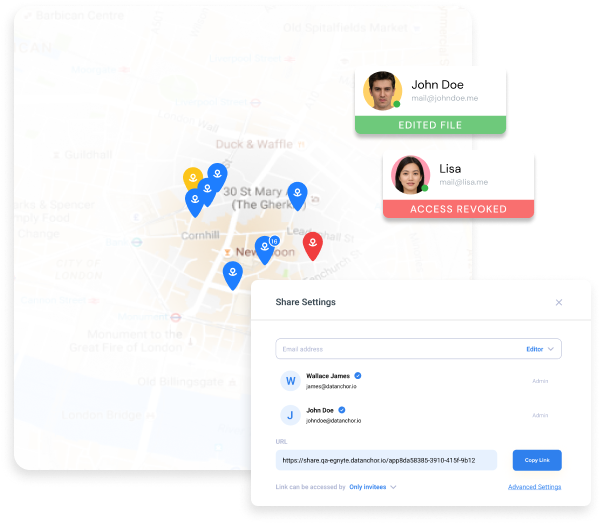
Digital Chain of Custody via Forensic Logging
Real-time tracking of sensitive data. Audit trails of each access, including physical location. A true chain of custody for digital data shared internally or outside of your organization- transparency at its finest.
Sign Up for a Demo
Real-time tracking of sensitive data. Audit trails of each access, including physical location.